In a previous blog post, I demonstrated how to effortlessly set up Portainer and an Odoo instance, providing you with a powerful platform for managing your Odoo container. Another crucial aspect of running a containerized application like Odoo is ensuring that it is easily accessible and secure. This is where Traefik comes in. Traefik is a modern, dynamic reverse proxy and load balancer designed specifically for containerized applications. As a reverse proxy, Traefik routes requests from clients to the appropriate backend services, effectively handling incoming traffic and distributing it to the right containers. This not only improves the performance and reliability of the application but also simplifies the process of managing multiple containers running different services. Additionally, Traefik provides built-in support for modern security features, such as automatic SSL certificate management, to ensure that your Odoo deployment remains secure and compliant.
In this blog post, I'll guide you through the process of installing Traefik in Portainer and configuring Let's Encrypt as a certificates resolver for secure SSL connections. I'll also demonstrate how to create routes to redirect HTTP traffic to HTTPS and update your Odoo container to utilize Traefik as a reverse proxy, ensuring a seamless and secure user experience for your Odoo instance.
Traefik configuration for the reverse proxy and SSL
In this section, I present the docker-compose.yml file designed to streamline the deployment of Traefik as a reverse proxy with SSL. This configuration ensures a secure and efficient setup for your services, such as Odoo, while also integrating seamlessly with Let's Encrypt for automated SSL certificate management.
version: '3'
services:
traefik:
image: traefik:v2.5.6
container_name: traefik
restart: unless-stopped
networks:
- web
command:
- --log=true
- --log.level=DEBUG
- --accessLog=true
- --accessLog.filePath=/logs/traefik.log
- --accessLog.bufferingSize=100
- --accessLog.filters.statusCodes=400-530
- --api=true
- --api.dashboard=true
- --api.insecure=true
- --providers.docker=true
- --providers.docker.exposedbydefault=false
- --providers.docker.watch=true
- --entrypoints.http.address=:80
- --entrypoints.https.address=:443
- --certificatesresolvers.letsencrypt.acme.httpchallenge=true
- --certificatesresolvers.letsencrypt.acme.httpchallenge.entrypoint=http
- --certificatesResolvers.letsencrypt.acme.email=your@email.com
- --certificatesResolvers.letsencrypt.acme.storage=/letsencrypt/acme.json
volumes:
- /etc/localtime:/etc/localtime:ro
- /var/run/docker.sock:/var/run/docker.sock:ro
- traefik2_letsencrypt:/letsencrypt
- traefik2_logs:/logs
labels:
- "traefik.enable=true"
# HTTP-to-HTTPS Redirect
- "traefik.http.routers.http-catchall.entrypoints=http"
- "traefik.http.routers.http-catchall.rule=HostRegexp(`{host:.+}`)"
- "traefik.http.routers.http-catchall.middlewares=redirect-to-https"
- "traefik.http.middlewares.redirect-to-https.redirectscheme.scheme=https"
ports:
- 80:80
- 443:443
- 8080:8080
volumes:
traefik2_letsencrypt:
external: true
traefik2_logs:
external: true
networks:
web:
external: true
name: webThis docker-compose.yml file sets up Traefik v2.5.6 as a reverse proxy with Let's Encrypt for SSL certificate management. The Traefik container is configured to restart unless stopped and connected to the "web" network. Logging and access logging are enabled, along with the API dashboard in insecure mode. Traefik is set up to watch Docker containers, with default exposure disabled.
SSL certificate management
For the SSL certificate management, HTTP and HTTPS entry points are defined, and Let's Encrypt is configured to use the ACME HTTP challenge with a specified email address for certificate storage:
- The certificatesresolvers.letsencrypt.acme.httpchallenge=true flag enables the ACME HTTP challenge, which is a method of validating domain ownership by responding to specific HTTP requests made by the ACME server. It allows Traefik to automatically request and renew SSL certificates for your domain.
- The certificatesresolvers.letsencrypt.acme.httpchallenge.entrypoint=http line specifies that the entry point for the ACME HTTP challenge should be the "http" entry point, specified above at port 80. This is where the ACME server will send its challenge requests, which Traefik will respond to for validation.
- The certificatesResolvers.letsencrypt.acme.email=your@email.com flag sets the email address associated with your Let's Encrypt account. This email is used for account recovery, expiration notifications, and other important communications.
- The certificatesResolvers.letsencrypt.acme.storage=/letsencrypt/acme.json line defines the storage location for the ACME account and SSL certificate data, in this case, the /letsencrypt/acme.json file within the container. This file will contain the SSL certificates, private keys, and other related information, which should be kept secure and backed up as needed.
Reverse proxy
The labels in the docker-compose.yml enable the reverse proxy and set up an HTTP-to-HTTPS redirect:
- The traefik.enable=true label activates Traefik for the specific container. Since Traefik is configured with exposedbydefault=false, you must explicitly enable Traefik for each container you want it to manage by setting this label to "true".
- The traefik.http.routers.http-catchall.entrypoints=http label defines a catch-all HTTP router called "http-catchall" that listens on the "http" entry point, specified above at port 80. This router is responsible for handling incoming HTTP requests.
- The traefik.http.routers.http-catchall.rule=HostRegexp({host:.+}) label sets the rule for the "http-catchall" router to match any host, indicated by the regular expression {host:.+}. This means that the router will catch all incoming HTTP requests regardless of the requested domain.
- The traefik.http.routers.http-catchall.middlewares=redirect-to-https label associates the "http-catchall" router with a middleware called "redirect-to-https". The middleware will process the requests caught by the router and perform specific actions, such as redirection in this case.
- The traefik.http.middlewares.redirect-to-https.redirectscheme.scheme=https label configures the "redirect-to-https" middleware to change the request scheme to "https" before redirecting. In other words, this middleware will redirect all incoming HTTP requests to their HTTPS equivalents, ensuring that all traffic is securely encrypted.
Deploying Traefik in Portainer
Portainer simplifies the process of deploying your docker-compose.yml file, making it a breeze to set up your Traefik reverse proxy with SSL. To get started, log in to your Portainer instance and navigate to the "Stacks" section. Click on "Add Stack" and, in the provided text area, copy and paste the contents of your docker-compose.yml file. Make sure to replace any placeholder values, such as the email address for Let's Encrypt, with your actual information. Once you've reviewed the configuration, click "Deploy the Stack" to initiate the deployment process. Portainer will automatically create and configure the necessary containers, networks, and volumes, bringing your Traefik reverse proxy to life.
Once you've successfully deployed the stack using Portainer, you can easily access the Traefik dashboard to monitor and manage your reverse proxy. To do so, open your web browser and navigate to the IP address or domain name of the server running your Traefik instance, followed by the port number specified in the docker-compose.yml file for the dashboard (in our example, it's port 8080). For instance, if your server's IP address is localhost, you would access the Traefik dashboard by visiting http://localhost:8080. You'll be greeted by the Traefik dashboard, where you can view the status of your routers, middlewares, services, and more.
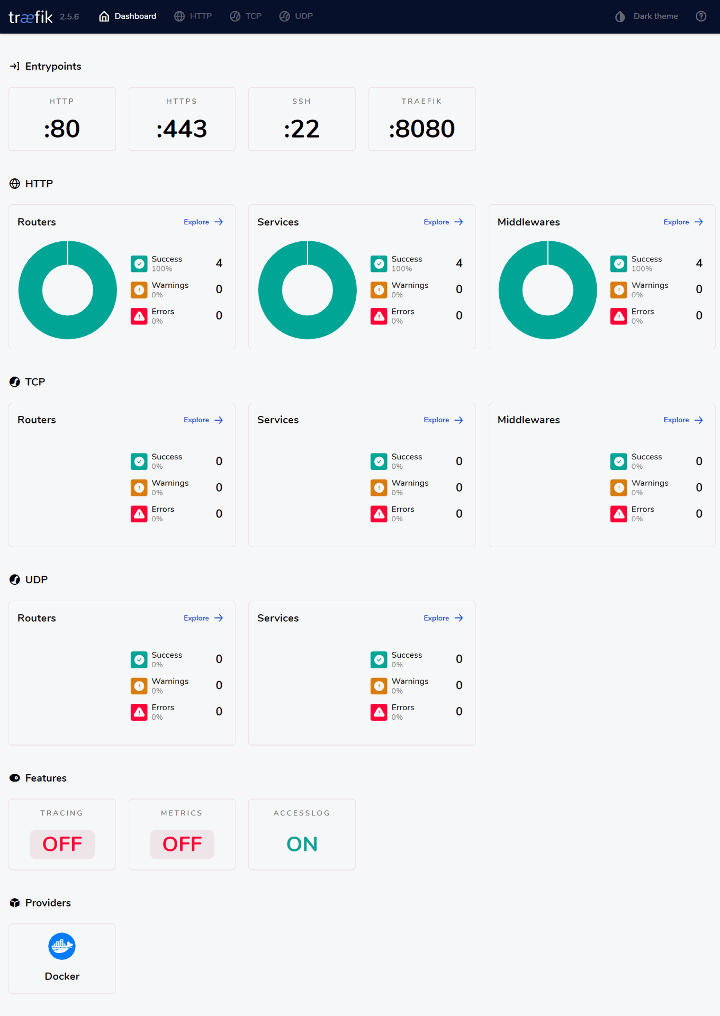
Note
Please note that the Traefik Dashboard is configured in insecure mode. This is not recommended in a production environment. However, the specifics of configuring a secure Dashboard fall beyond the scope of this blog post. See the following link for more information on how to configure the Dashboard in secure mode: https://doc.traefik.io/traefik/operations/dashboard/#secure-mode
Configuring the reverse proxy and SSL for your Odoo instance
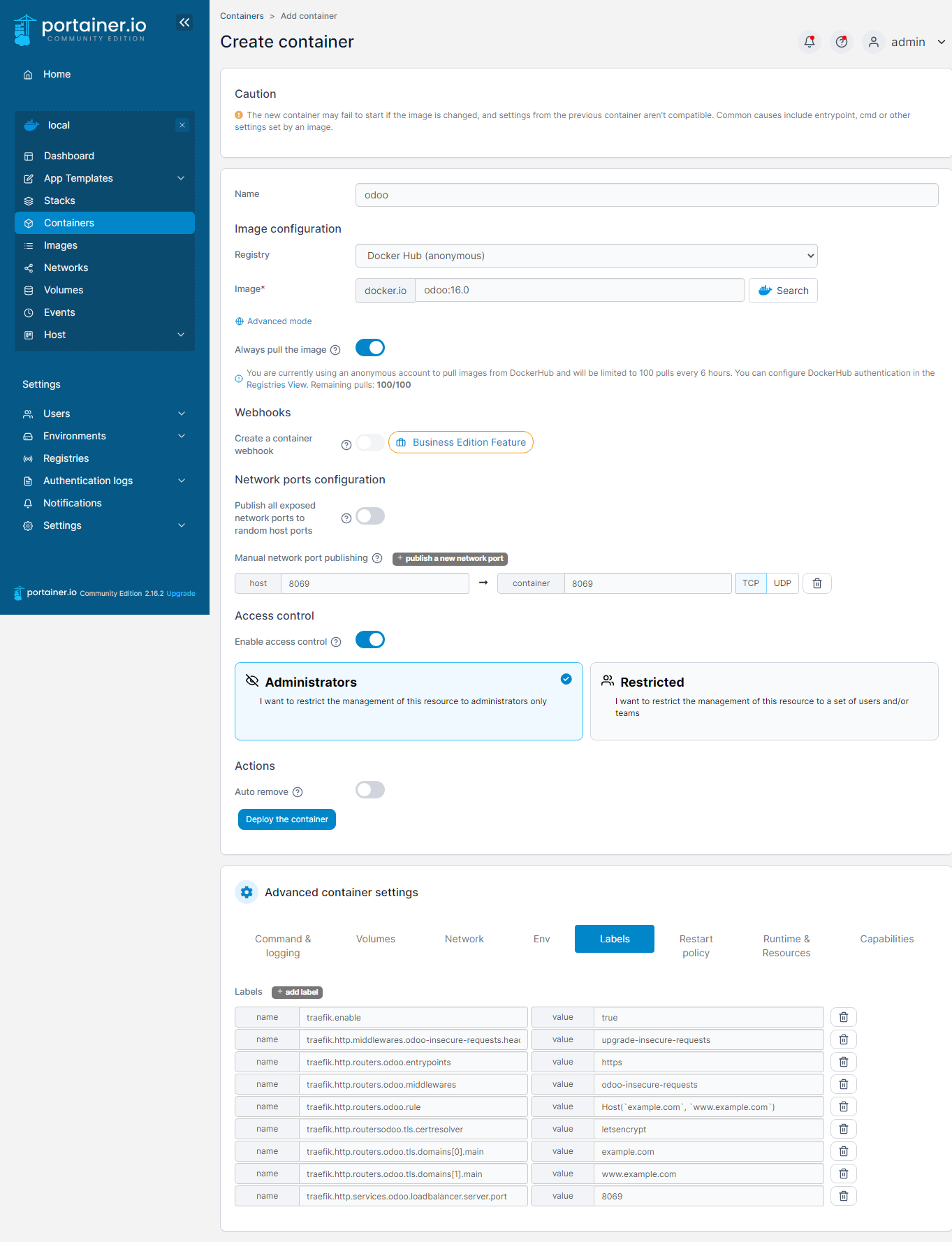
Configuring Traefik to work seamlessly with an Odoo container can be achieved by adding the necessary labels to the docker-compose.yml file of your Odoo stack or by editing an existing Odoo instance in Portainer.
labels:
- "traefik.enable=true"
- "traefik.http.middlewares.odoo-headers.headers.contentSecurityPolicy=upgrade-insecure-requests"
- "traefik.http.routers.odoo.entrypoints=https"
- "traefik.http.routers.odoo.middlewares=odoo-headers"
- "traefik.http.routers.odoo.rule=Host(`example.com`, `www.example.com`)"
- "traefik.http.routers.odoo.tls.certresolver=letsencrypt"
- "traefik.http.routers.odoo.tls.domains[0].main=example.com"
- "traefik.http.routers.odoo.tls.domains[1].main=www.example.com"
- "traefik.http.services.odoo.loadbalancer.server.port=8069"These Traefik labels define the configuration for an Odoo instance, including enabling Traefik, setting up middlewares, routers, and services, and configuring SSL certificates:
- The traefik.enable=true label activates Traefik for the specific container, ensuring that Traefik manages this instance.
- The traefik.http.middlewares.odoo-header.headers.contentSecurityPolicy=upgrade-insecure-requests label configures a middleware called "odoo-headers" to enforce the Content Security Policy header with the value "upgrade-insecure-requests". This header instructs the browser to upgrade any insecure HTTP requests to HTTPS before making the request.
- The traefik.http.routers.odoo.entrypoints=https label defines an HTTPS router named "odoo" that listens on the "https" entry point on port 443.
- The traefik.http.routers.odoo.middlewares=odoo-headers label associates the "odoo" router with the "odoo-headers" middleware, which will process requests caught by the router to upgrade insecure requests.
- The traefik.http.routers.odoo.rule=Host(`example.com`, `www.example.com`) label sets the rule for the "odoo" router to match the specified hostnames: "example.com" and "www.example.com". The router will catch incoming requests for these domains.
- The traefik.http.routers.odoo.tls.certresolver=letsencrypt label specifies that the "odoo" router should use the "letsencrypt" certificate resolver for obtaining SSL certificates.
- The traefik.http.routers.odoo.tls.domains[0].main=example.com and traefik.http.routers.odoo.tls.domains[1].main=www.example.com labels define the primary domain names for which the SSL certificates should be obtained: "example.com" and "www.example.com".
- The traefik.http.services.odoo.loadbalancer.server.port=8069 label configures the "odoo" service, setting the load balancer's target server port to 8069, which is the default port for Odoo instances.
To incorporate Traefik in your docker-compose.yml file, simply add the labels described above to the 'labels' section of the Odoo service. Ensure that the domain names and any other settings match your specific requirements. If you're using Portainer, navigate to the Odoo container's details, click "Duplicate/Edit," and add the labels under the "Labels" tab. Save the changes and recreate the container to apply the new settings. With these labels in place, Traefik will now manage the routing, SSL certificates, and security configurations for your Odoo container, creating a secure and optimized environment for Odoo.
With the Odoo container deployed, you now have a fully functional Odoo instance with Traefik configured as a secure SSL reverse proxy. You should now be able to access your Odoo container on example.com with SSL enabled by default.
Conclusion
Setting up Traefik as a reverse proxy and configuring it for your Odoo instance greatly enhances the security, performance, and management of your web services. With Traefik in place, you benefit from automated SSL certificate management, efficient routing, and the ability to seamlessly upgrade insecure requests. The integration with Portainer or the use of a docker-compose.yml file simplifies deployment and maintenance. Overall, Traefik and Odoo integration creates a reliable and secure foundation for your business operations, allowing you to focus on what truly matters: growing your business.